
4.5 MC Answers and Review
7 min read•march 13, 2023
Answers and Review for Multiple Choice Practice on Computer Systems & Networks

Image courtesy of Pixabay
⛔STOP ⛔ Before you look at the answers, make sure you gave this practice quiz a try so you can assess your understanding of the concepts covered in Big Idea 4. Click here for the practice questions: AP CS: Principles Big Idea 4 Multiple Choice Questions.
Facts about the test: The AP CS: Principles exam has 70 multiple choice questions and you will be given 2 hours (120 minutes) to complete the section. That means it should take you around 10 minutes to complete 6 questions. The following questions were not written by College Board and, although they cover information outlined in the AP Computer Science Principles Course and Exam Description, the formatting on the exam may be different.
A. There is not an algorithm that can solve it
B. It is solved most efficiently with large databases
C. Multiple algorithms exist with different levels of efficiency
D. The solution is too inefficient for large databases
Explanation: Intractable problems might have an algorithm that can solve some or a small number of values, but as the dataset gets large, the algorithm won't work due to a lack of resources, either memory or storage.
Watch this review of Big Idea 4!
2. How does the internet work with the different equipment in use?
A. Vendors follow the protocols established to enable data to be sent & received across any equipment
B. The routers adjust for the different equipment manufacturers by sending data on the same equipment brands
C. Specific companies are approved to make equipment for the Internet
D. The server farms handle the data once the data reach Regional ISP (Internet Service Provider)
Explanation: Protocols are a set of rules for different services on the Internet. Data will move across any brand of equipment as long as the protocols are followed.
Read this guide on the internet!
3. What is the most common way computer viruses are spread?
A. From pop-up ads
B. Through network worms
C. By people clicking on an infected file
D. From random botnet attacks
Explanation: Viruses are spread via an infected file. These are transmitted in ways to get people to click on them.
Read this guide on safe computing!
4. What does Moore's Law indicate?
A. That the size of computers would decrease by half every two years
B. The power of the processors would double approximately every 2 years
C. That the price of computers would decrease by half every two years
D. That the cost of computer storage would decrease by half every two years
Explanation: Moore's law indicates that the number of transistors that can fit on a circuit has doubled about every 2 years, which leads to faster processors.
Watch this review of Big Idea 4!
5. When would lossless data compression be preferred over a lossy one?
A. When you need to get back to the original file
B. When you do not need to get back to the original file
C. When you need to display the file on mobile devices and websites
D. When you have limited space available on your computer
Explanation: lossless data compression techniques enable the original, uncompressed file to be restored. Lossless techniques don't provide as much compression as a lossy technique, but always select this when you might need to restore an original file
Read this guide on Data Compression!
6. When does cryptography enable the Internet to process transactions securely?
A. Symmetric keys are used to encrypt & decrypt messages for speed in processing to avoid being intercepted
B. Frequency analysis is used to disguise the use of common letters in encrypted messages keeping passwords secure
C. The public key encryption model is easy to use to encrypt data but intractable to decrypt for large numbers
D. Polynumeric alphabets are used to encrypt & decrypt messages to allow for use with different languages
Explanation: A good cryptographic model is easy to use in one direction, but difficult in the other.. if the information is intercepted, identifying the correct encryption key would make it tough.
Read this guide on safe computing!
7. A camera watching an eagle's nest starts recording when a motion detector starts. Which of the following is the metadata?
A. The number of eagles using the nest
B. The data & time the motion is detected
C. The latitude & longitude of the nest
D. The number of frames per second the camera records
Explanation: Metadata is data about the data, which would be the number of frames the camera can record.
Read this guide about metadata!
8. Suzie's mother wants a copy of a photo from a family vacation they took. The picture is too large to email. How should she compress the image to print a large copy of it suitable for framing?
A. She should combine lossy & lossless compression to get enough compression to send the image
B. She should use lossy compression to get enough compression to send the image
C. She should use a lossless compression, which will help print a version with high enough quality to frame
D. Any compression will be sufficient in this case
Explanation: Only lossless compression will allow the original uncompressed photo to be restored.
Read this guide on Data Compression!
9. When listening to an online music service, you request songs "like" a specific song. How does the music site determine which songs to play?
A. It plays the most requested songs from all listeners
B. It plays songs you have played recently
C. It uses data-mining to determine patterns in the music that are similar
D. It plays a random selection
Explanation: Data mining identifies patterns & correlations among the data that can show similarities between songs.
Read this guide on using data!
10. How do the world wide web and the Internet work together?
A. The internet has the "deep" net and "dark" net but the Web does not
B. The internet uses the web to connect devices to share data
C. The web uses HTTP to share computational artifacts using the Internet
D. They perform the same functionality
Explanation: The WWW is an application that uses HTTP to share documents, videos, images, and other files among devices connected to the internet.
Read this guide on the internet!
11. If a fire happens at a major Internet hub, what is the result?
A. Different IP addresses will be assigned to devices that were impacted by the unavailability of the hub
B. The part of the globe that is served by that hub will be down because of the end-to-end architecture of the Internet
C. Internet traffic will be routed a different way because of the redundancy built into the Internet
D. People can use dedicated phone lines as a backup with no change in service
Explanation: The redundancy designed into the Internet means data can be sent via different paths to reach its destination.
Read this guide on the internet!
12. In the following web address, how many domain levels are there?: http://anytime.anyway.anyplace.edu/lessons/notes/apex.docx
A. 3
B. 4
C. 5
D. 6
Explanation: Domain levels go from Top-level Domain (.edu) to the left.
Read this guide on the internet!
13. If a company is trying to determine whether to upgrade its bandwidth based on the following graph (see image), what should they measure?
A. Amount of data downloaded as it has the largest impact on the bandwidth
B. Frequency of the peak times
C. Amount of data uploaded as this includes strategic company backup data
D. Type of devices employees use on the network
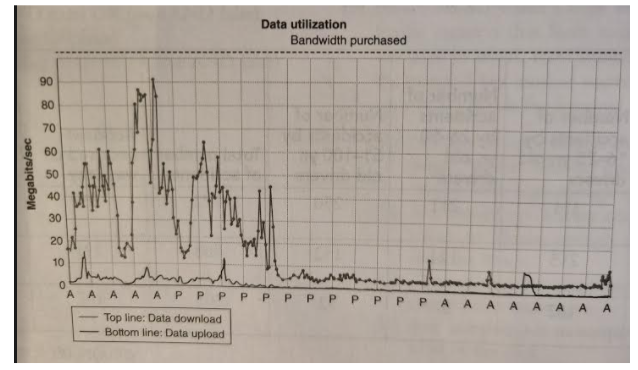
Explanation: Bandwidth measures the amount of data that can be transmitted in a specific amount of time.
Read this guide on the internet!
14. Which of the following is true about packets?
A. Packets are reassembled at their final destination
B. The receiving device acknowledges the first & last packets to indicate receipt of the data stream
C. Packets travel in order to their destination
D. Packets follow the shortest path to their destination
Explanation: Packets are created at the sending end of the transmission & reassembled at the final destination.
Read this guide on Fault Tolerance and Packets
15. How do TCP and IP interact?
A. IP forwards the data to the DNS server to identify which TCP to use.
B. TCP creates packets from the data to be sent and transfers control to IP for routing. TCP then reassembles the packets at the destination
C. TCP hands off control to HTTP, which passes it to IP.
D. IP uses the SSL in conjunction with TCP to securely send data.
Explanation: TCP creates packets and passes control of them to IP, which routes them to their final destination. TCP then reassembles the packets to display.
Read this guide on the internet!
What can we help you do now?
- 🔍Check out all of the resources for AP CS: P Big Idea 5
- 🦘Jump to AP CS: P Big Idea 5 Multiple Choice Questions
🤝Connect with other students studying AP CS: P with Hours
4.5 MC Answers and Review
7 min read•march 13, 2023
Answers and Review for Multiple Choice Practice on Computer Systems & Networks

Image courtesy of Pixabay
⛔STOP ⛔ Before you look at the answers, make sure you gave this practice quiz a try so you can assess your understanding of the concepts covered in Big Idea 4. Click here for the practice questions: AP CS: Principles Big Idea 4 Multiple Choice Questions.
Facts about the test: The AP CS: Principles exam has 70 multiple choice questions and you will be given 2 hours (120 minutes) to complete the section. That means it should take you around 10 minutes to complete 6 questions. The following questions were not written by College Board and, although they cover information outlined in the AP Computer Science Principles Course and Exam Description, the formatting on the exam may be different.
A. There is not an algorithm that can solve it
B. It is solved most efficiently with large databases
C. Multiple algorithms exist with different levels of efficiency
D. The solution is too inefficient for large databases
Explanation: Intractable problems might have an algorithm that can solve some or a small number of values, but as the dataset gets large, the algorithm won't work due to a lack of resources, either memory or storage.
Watch this review of Big Idea 4!
2. How does the internet work with the different equipment in use?
A. Vendors follow the protocols established to enable data to be sent & received across any equipment
B. The routers adjust for the different equipment manufacturers by sending data on the same equipment brands
C. Specific companies are approved to make equipment for the Internet
D. The server farms handle the data once the data reach Regional ISP (Internet Service Provider)
Explanation: Protocols are a set of rules for different services on the Internet. Data will move across any brand of equipment as long as the protocols are followed.
Read this guide on the internet!
3. What is the most common way computer viruses are spread?
A. From pop-up ads
B. Through network worms
C. By people clicking on an infected file
D. From random botnet attacks
Explanation: Viruses are spread via an infected file. These are transmitted in ways to get people to click on them.
Read this guide on safe computing!
4. What does Moore's Law indicate?
A. That the size of computers would decrease by half every two years
B. The power of the processors would double approximately every 2 years
C. That the price of computers would decrease by half every two years
D. That the cost of computer storage would decrease by half every two years
Explanation: Moore's law indicates that the number of transistors that can fit on a circuit has doubled about every 2 years, which leads to faster processors.
Watch this review of Big Idea 4!
5. When would lossless data compression be preferred over a lossy one?
A. When you need to get back to the original file
B. When you do not need to get back to the original file
C. When you need to display the file on mobile devices and websites
D. When you have limited space available on your computer
Explanation: lossless data compression techniques enable the original, uncompressed file to be restored. Lossless techniques don't provide as much compression as a lossy technique, but always select this when you might need to restore an original file
Read this guide on Data Compression!
6. When does cryptography enable the Internet to process transactions securely?
A. Symmetric keys are used to encrypt & decrypt messages for speed in processing to avoid being intercepted
B. Frequency analysis is used to disguise the use of common letters in encrypted messages keeping passwords secure
C. The public key encryption model is easy to use to encrypt data but intractable to decrypt for large numbers
D. Polynumeric alphabets are used to encrypt & decrypt messages to allow for use with different languages
Explanation: A good cryptographic model is easy to use in one direction, but difficult in the other.. if the information is intercepted, identifying the correct encryption key would make it tough.
Read this guide on safe computing!
7. A camera watching an eagle's nest starts recording when a motion detector starts. Which of the following is the metadata?
A. The number of eagles using the nest
B. The data & time the motion is detected
C. The latitude & longitude of the nest
D. The number of frames per second the camera records
Explanation: Metadata is data about the data, which would be the number of frames the camera can record.
Read this guide about metadata!
8. Suzie's mother wants a copy of a photo from a family vacation they took. The picture is too large to email. How should she compress the image to print a large copy of it suitable for framing?
A. She should combine lossy & lossless compression to get enough compression to send the image
B. She should use lossy compression to get enough compression to send the image
C. She should use a lossless compression, which will help print a version with high enough quality to frame
D. Any compression will be sufficient in this case
Explanation: Only lossless compression will allow the original uncompressed photo to be restored.
Read this guide on Data Compression!
9. When listening to an online music service, you request songs "like" a specific song. How does the music site determine which songs to play?
A. It plays the most requested songs from all listeners
B. It plays songs you have played recently
C. It uses data-mining to determine patterns in the music that are similar
D. It plays a random selection
Explanation: Data mining identifies patterns & correlations among the data that can show similarities between songs.
Read this guide on using data!
10. How do the world wide web and the Internet work together?
A. The internet has the "deep" net and "dark" net but the Web does not
B. The internet uses the web to connect devices to share data
C. The web uses HTTP to share computational artifacts using the Internet
D. They perform the same functionality
Explanation: The WWW is an application that uses HTTP to share documents, videos, images, and other files among devices connected to the internet.
Read this guide on the internet!
11. If a fire happens at a major Internet hub, what is the result?
A. Different IP addresses will be assigned to devices that were impacted by the unavailability of the hub
B. The part of the globe that is served by that hub will be down because of the end-to-end architecture of the Internet
C. Internet traffic will be routed a different way because of the redundancy built into the Internet
D. People can use dedicated phone lines as a backup with no change in service
Explanation: The redundancy designed into the Internet means data can be sent via different paths to reach its destination.
Read this guide on the internet!
12. In the following web address, how many domain levels are there?: http://anytime.anyway.anyplace.edu/lessons/notes/apex.docx
A. 3
B. 4
C. 5
D. 6
Explanation: Domain levels go from Top-level Domain (.edu) to the left.
Read this guide on the internet!
13. If a company is trying to determine whether to upgrade its bandwidth based on the following graph (see image), what should they measure?
A. Amount of data downloaded as it has the largest impact on the bandwidth
B. Frequency of the peak times
C. Amount of data uploaded as this includes strategic company backup data
D. Type of devices employees use on the network

Explanation: Bandwidth measures the amount of data that can be transmitted in a specific amount of time.
Read this guide on the internet!
14. Which of the following is true about packets?
A. Packets are reassembled at their final destination
B. The receiving device acknowledges the first & last packets to indicate receipt of the data stream
C. Packets travel in order to their destination
D. Packets follow the shortest path to their destination
Explanation: Packets are created at the sending end of the transmission & reassembled at the final destination.
Read this guide on Fault Tolerance and Packets
15. How do TCP and IP interact?
A. IP forwards the data to the DNS server to identify which TCP to use.
B. TCP creates packets from the data to be sent and transfers control to IP for routing. TCP then reassembles the packets at the destination
C. TCP hands off control to HTTP, which passes it to IP.
D. IP uses the SSL in conjunction with TCP to securely send data.
Explanation: TCP creates packets and passes control of them to IP, which routes them to their final destination. TCP then reassembles the packets to display.
Read this guide on the internet!
What can we help you do now?
- 🔍Check out all of the resources for AP CS: P Big Idea 5
- 🦘Jump to AP CS: P Big Idea 5 Multiple Choice Questions
🤝Connect with other students studying AP CS: P with Hours

Resources
© 2024 Fiveable Inc. All rights reserved.
AP® and SAT® are trademarks registered by the College Board, which is not affiliated with, and does not endorse this website.